The GDPR bluff: Why a server in Frankfurt won't automatically save you (and encryption is more than just a tick box)
Discussions about GDPR compliance in the cloud often end in a dead end of country abbreviations: „US cloud bad, EU cloud good.“ But reducing cloud security to geography overlooks the crucial technical point: Who actually controls the data while it is being processed?
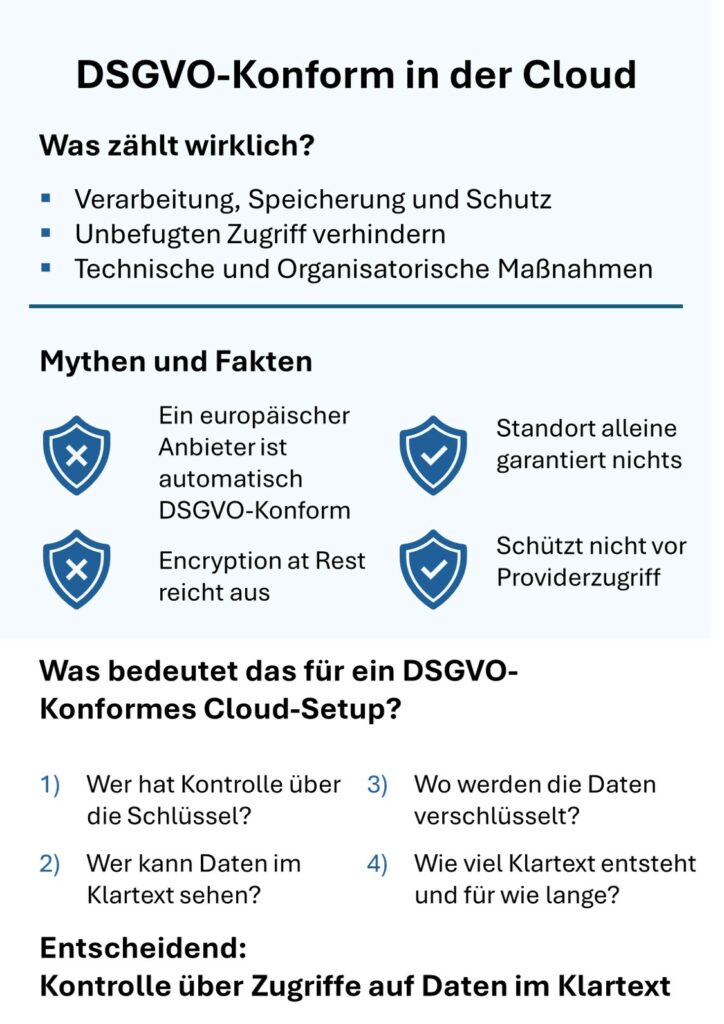
The reality is inconvenient: a German location is not a security feature, and a US provider is not an automatic risk. What counts is the architecture.
Let's dispel three dangerous myths.
Myth 1: „A European provider is automatically secure and GDPR-compliant“
This is perhaps the biggest fallacy. It is an unpleasant truth that is rarely spoken out loud in the industry: A data center in Germany does not guarantee modern security standards.
Time and again, we see „sovereign cloud“ providers who proudly claim to be GDPR compliant, but are years behind in terms of technology.
- Lack of encryption: Some local „public clouds“ do not even offer a standard Encryption at Rest a feature that has been a standard feature of hyperscalers for over a decade.
- Outdated admin architectures: Without modern hardware isolation (such as the AWS Nitro system), administrative access to servers is often much easier than with global platforms.
The provocative question is: What do you prefer? A provider in Frankfurt whose admins could theoretically access your unencrypted data via SSH because the architecture is outdated? Or a US provider that technically locks itself out and cannot access your data at all? can?
GDPR compliance requires „appropriate technical and organizational measures“ (TOMs). A provider that does not provide this technology is not compliant - no matter how German its postal address is.
Myth 2: „Encryption at rest is enough.“
Many companies check the „Encryption at rest“ box and sit back. This is negligent.
- The problem: With standard encryption (managed keys), the provider controls the keys.
- The consequence: If an authority (whether from the USA or Europe) demands the release of data, the provider can be technically forced to decrypt it.
- Conclusion: Encryption at Rest protects you from the theft of a hard disk from the data center, but not from a legal order to hand over data.
Myth 3: „US clouds are illegal because of the CLOUD Act.“
The CLOUD Act is a risk, but not a blanket ban. It only applies if the provider has access to the data („Possession, Custody, or Control“). The solution is technical, not political: if you manage the keys in such a way that the provider has no technical access to the plaintext, a disclosure order will be in vain. Where there is no access, nothing can be released.
The real challenge: data-in-use & the „kill switch“
The GDPR is less interested in geography than in the question: Who controls the plain text? This is where two technologies come into play that enable true digital sovereignty:
- Hardware isolation instead of trust (The Nitro Principle)For a long time, the following was true: whoever runs the server can look into the RAM. This is wrong with modern architectures. Systems like the AWS Nitro Systemare designed in such a way that there is no administrative access (no SSH) for the cloud operator. Independent audits (e.g. NCC Group) confirm that there is no mechanism by which an operator could read data in the storage („zero operator access“). This also protects data during processing.
- The ultimate emergency stop: External Key Stores (XKS)You only have real sovereignty when you remove the „root of trust“ from the cloud. With a External Key Store (XKS)the keys are stored in your own hardware security module (or with a trustee) - never in the cloud.
- The effect: When AWS needs to process data, they request your key for a short time.
- The kill switch: If you disconnect from your keystore, all data in the cloud immediately becomes unreadable junk data.
- Legal consequence: Even under duress can the provider does not release any readable data to the authorities because it does not have the key.
Sovereignty is an architectural decision
GDPR-compliant cloud use is possible - even with US hyperscalers. But it doesn't happen by itself.
Stop relying on location. Ask the hard technical questions instead:
- Who has the key? (The answer must be: Me - or a trustee, not the cloud provider alone).
- Is there hardware isolation? (Protection against admin access in the data center.)
- What happens if I pull the plug? (Is the data then unreadable?)
Those who answer these questions in a technically sound manner will build a fortress that is more secure and compliant than many a „sovereign cloud“, which only advertises its location but fails when it comes to security.
Digital sovereignty does not start on the map. It begins in the architecture.
If you want to know more about safe Cloud architectures and data protection, we recommend that you read our other Technical article on the website. There we offer in-depth analyses and practical solutions for your digital sovereignty.


